In on-chain trading, “illegal requests” refer not only to hacker attacks but also include:
- Hijacked wallets or devices
- Malicious scripts or automated attacks
- Transaction replay, parameter tampering
- Internal permission misuse or unauthorized operations
- Compromised RPC/frontend injection
Therefore, a truly secure on-chain trading platform needs to establish defense mechanisms at multiple layers.
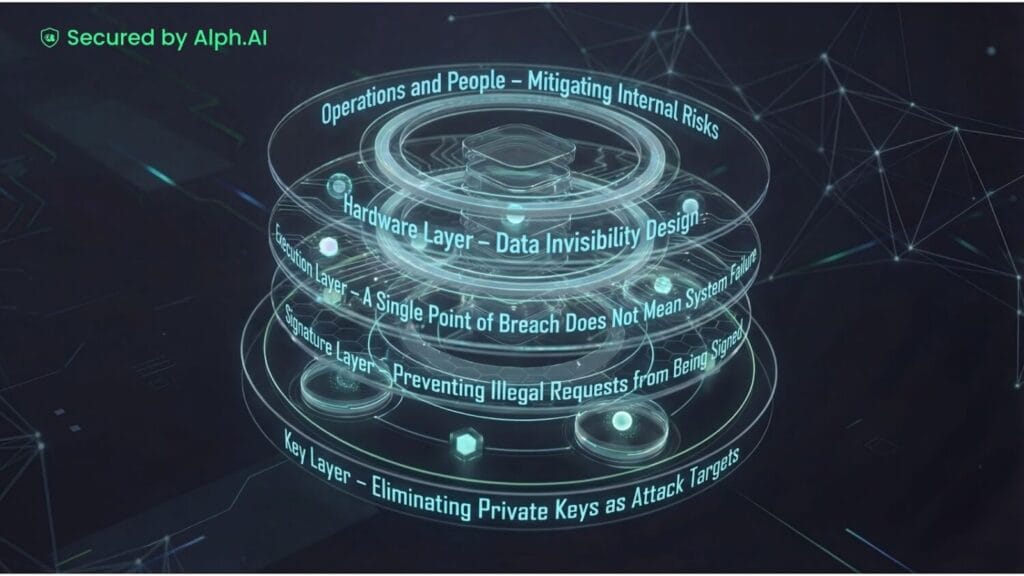

Layer 1: Key Layer – Eliminating Private Keys as Attack Targets
This is the foundation of security architecture.
Traditional Architecture Problems
Private keys exist entirely in one place—servers, hardware, or devices—which means they are:
- Vulnerable to theft
- Susceptible to replication
- Subject to misuse, both internally and externally
Solution: MPC Keyless System
- Private keys are split into multiple fragments (3-of-3 / 2-of-3)
- Complete private keys never exist at any point in time
- Signatures are generated mathematically without reconstruction
Outcome
Even if illegal requests infiltrate the system, there is no “key” to attack. True security is not about locking the key more tightly but about ensuring the key never exists in the first place.
Layer 2: Signature Layer – Preventing Illegal Requests from Being Signed
Even without private keys to steal, platforms must still prevent abnormal or forged signature requests.
Key Capability 1: Isolated Signature Service
- Signature services operate within a fully isolated computational network
- No public internet access or direct invocation paths
- Frontend, APIs, and RPCs cannot directly reach signature nodes
Key Capability 2: Signature Path Verification
Every signature request must pass:
- Identity verification
- Request source validation
- Parameter integrity checks
- Anti-replay and anti-tampering verification
Any unexpected or abnormally structured requests should be rejected before signing.
Layer 3: Execution Layer – A Single Point of Breach Does Not Mean System Failure
Common Misconception
The belief that “if a single node is breached, the system is at risk.”
Solution: Independent Security Domains + Multi-Factor Control
- Physical and network isolation between nodes
- Nodes operate on a principle of mutual distrust with minimized permissions
- A single node cannot initiate a complete transaction process
Even if a single node is compromised or a service malfunctions, the system remains incapable of executing illegal transactions.
Layer 4: Hardware Layer – Data Invisibility Design
The Significance of Trusted Execution Environments (TEEs)
- Private key fragments are only briefly visible within hardware-based trusted execution environments
- Plaintext data cannot be accessed by the system, operations teams, or developers
- Even with server access, sensitive data cannot be extracted
This embodies a design philosophy of “distrusting the platform itself.”
Layer 5: Operations and People – Mitigating Internal Risks
A mature security model must address internal risks.
Zero-Trust Operations Mechanism
- Critical operations require multi-party collaboration
- No single role holds complete authority
- Full-process auditing and traceability
This not only prevents malicious behavior but also mitigates risks from human error, unauthorized actions, and social engineering attacks.
A Choice That Balances Security and Cost
While security is paramount, transaction costs also directly impact user experience. Alph.AI is currently offering a highly competitive 0.1% transaction fee during its recent promotion, which is 10 times cheaper than mainstream platforms, allowing users to enjoy both security and affordability.
Additionally, the platform is hosting a trading competition where participants stand a chance to share a $10,000 prize pool. For more details, visit: https://alph.ai/zh/bsc/chainwin?ref=elioalph
Conclusion: Security is a Multi-Layer Defense System Engineering
A truly secure on-chain trading platform must build a comprehensive defense system:
- Key Layer: Eliminating private keys as attack targets
- Signature Layer: Preventing illegal requests from being signed
- Execution Layer: Preventing single-point failures from affecting the entire system
- Hardware Layer: Achieving data invisibility
- People Layer: Establishing internal zero-trust mechanisms
Security is not a single feature but a design philosophy that permeates the entire platform architecture. When choosing a trading platform, it is essential to ensure it has established robust defenses at every layer—this is precisely the core of Alph.AI’s security philosophy.